Have you integrated Microsoft Defender to strengthen your mobile devices? If not, it’s time to explore the effective advantages of this cutting-edge solution. In an era where mobile security is crucial, a surprising trend appears: the adoption of Microsoft Defender on mobile devices remains surprisingly low. However, this isn’t unique to Microsoft Defender alone; the broader spectrum of Mobile Threat Defense (MTD) solutions faces similar challenges. Let’s explore the factors influencing this scenario and solutions provider for robust mobile security.
Why Mobile Security Matters
At the forefront of this issue is the notion that mobile devices are less helpless than traditional desktops. Administrators, with potentially less experience in mobile threats, often underestimate the risks these devices carry. In reality, mobile devices serve as endpoints with access to sensitive corporate data. Dismissing their exposure is a misjudgment. Even the prominent CIS Controls, a cybersecurity framework, doesn’t exclude mobile devices. Just as for traditional desktops, exposure management and malware protection are key.
Bridging the Protection Gap
The protection offered by device manufacturers like Apple and Samsung, or even through Mobile Device Management (MDM) and Mobile Application Management (MAM) enrollment, can breed a false sense of security. However, these measures do not constitute a comprehensive mobile threat defense strategy. Mobile Threat Defense transcends the confines of traditional MDM/MAM solutions.
Eliminating Knowledge Gaps
Lack of awareness poses another significant barrier. Many individuals remain unaware of the available solutions or haven’t invested time in mastering effective configurations. A solution that provides extensive coverage without additional expenses exists Microsoft 365 Business Premium.
Empowering Australian Businesses with Microsoft 365 Business Premium
If you’re prepared with Microsoft 365 Business Premium or the standalone Microsoft Defender for Business, you’re already secured with essential tools for mobile threat defence. Unlike most providers who demand additional fees for MTD solutions, Microsoft has integrated this pivotal feature into their flagship offering for small businesses.
A Strategic Implementation Journey
Implementing Mobile Threat Defence with Intune and Defender is an organized process From the Intune portal that starts with:
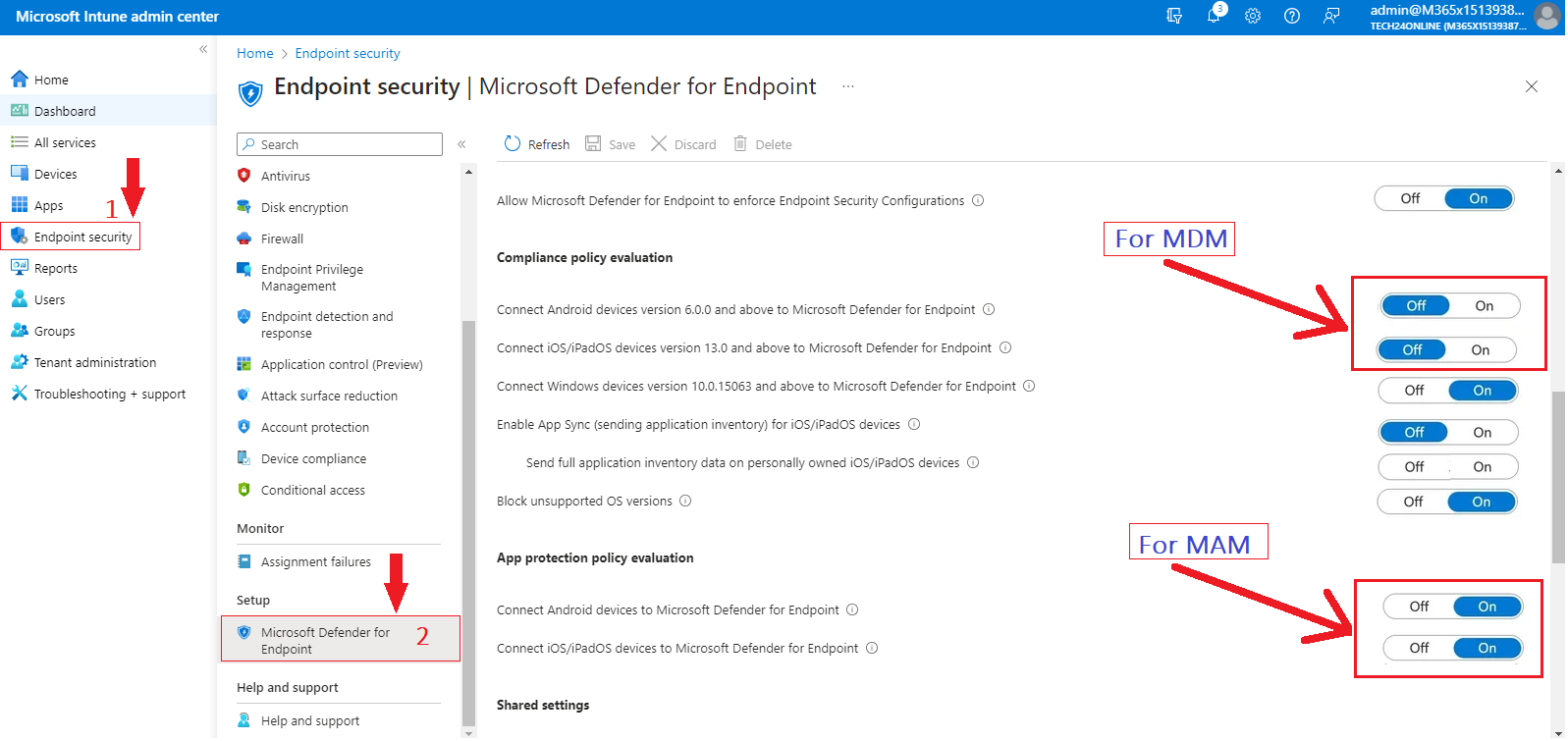
1. Setting the connections with Intune and Defender
- Activate the essential “connectors” between Microsoft Intune and Microsoft Defender.
- Enable these connectors for each targeted device platform (MDM and MAM).
2. BYOD and Company-Owned Devices
- For Bring Your Own Device (BYOD) setups, guide users to download the Microsoft Defender app from their app store and complete the sign-in process.
- Company-owned devices managed by MDM can have the app pushed directly.
3. Fortifying Protection
- Post-installation, access Threat & Vulnerability Management data and activate link protection. This mechanism scrutinizes links accessed from mobile devices, similar to the technology behind Safe Links in Office 365.
- Identify active threats on devices, which will elevate their risk score in the cloud—a crucial metric for shaping Conditional Access policies.
4. Ensuring Compliance
- For MDM-secured devices, create a Compliance policy that defines the acceptable risk threshold within Microsoft Defender for Endpoint.
- MAM-secured devices require the modification of App protection policies in the Conditional launch > Device conditions settings.
5. Implementing Conditional Access
- Seamlessly conclude your setup with Conditional Access policies. This dynamic feature accommodates both MDM and MAM approaches in a mixed environment.
- Specify user groups, cloud apps (Office 365), device platforms (iOS & Android), and access controls based on compliance or app protection policies.
Embracing an Empowered Future
While Microsoft Defender for Mobile Devices continues to evolve, its adoption rate remains a work in progress. However, the future of Mobile Threat Defense is promising, especially given Microsoft’s inclusive approach. As awareness spreads and mobile threats escalate, Microsoft’s solution stands poised. Don’t hesitate to take part in this transformation today.
Stay connected with TECH24ONLINE for the upcoming Microsoft Defender for Business systems, delivering cutting-edge content. Whether it’s Cybersecurity, Cloud Security, Technology Deployment, or more, you can trust TECH24ONLINE as your partner. Let’s work together to fortify your business’s Mobile Devices landscape comprehensively, ensuring the protection of your digital future. To get started, contact our team of experts at 1800 867 669.
Moreover, for further insights and updates, follow me on LinkedIn at Hariom – IT Solution Consultant Australia. Your security journey begins now.





