In an increasingly digital world, the importance of robust cyber security cannot be overstated. As businesses and organizations rely more on technology, they become more susceptible to cyber threats. To mitigate these risks and protect sensitive data, it’s crucial to implement effective security measures. One such approach gaining prominence is the “Essential 8 Security Framework.” In this comprehensive guide, we explore this framework, its key components, and how it can safeguard your organization from evolving cyber threats.
Understanding the Cyber Landscape

Cyber threats are constantly evolving, becoming more sophisticated and dangerous. Hackers and malicious actors are always looking for vulnerabilities to exploit, making it essential for organizations to stay one step ahead in their cyber security efforts.
The Essential 8 Security Framework
The Essential 8 Security Framework is a comprehensive guide developed by the Australian Cyber Security Centre (ACSC). It provides organizations with a structured approach to enhance their cyber security posture. Let’s delve into the eight key strategies within this framework:
1. Application Whitelisting

Application Whitelisting is a proactive approach to security that allows only approved applications to run on a system. By creating a list of trusted applications, organizations can prevent unauthorized software from executing, minimizing the risk of malware and other threats.
2. Patch Applications
Patching Applications involves keeping software and applications up to date with the latest security patches. Outdated software can contain vulnerabilities that cybercriminals can exploit. Regular updates are essential to close these security gaps.
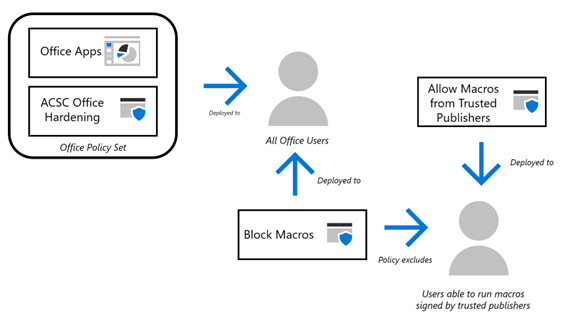
3. Configure Microsoft Office Macro Settings
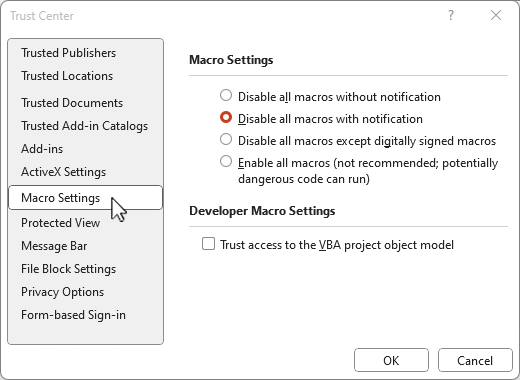
Cybercriminals often use Microsoft Office macros to deliver malware. The Essential 8 Framework recommends Configuring Microsoft Office Macro Settings to prevent macros from running without your approval.
4. User Application Hardening

User Application Hardening involves configuring web browsers and email client applications to block potentially harmful content. By doing so, organizations can reduce the risk of malware infections.
5. Restrict Administrative Privileges
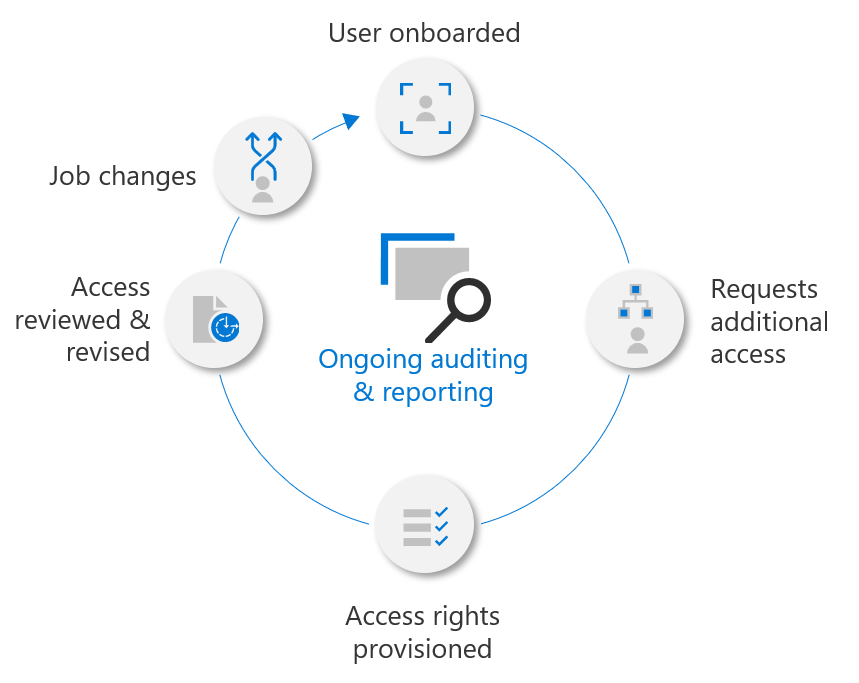
Restricting Administrative Privileges is a fundamental security practice. Limiting access to administrative functions to only those who require them can prevent unauthorized changes and protect critical systems.
6. Patch Operating Systems
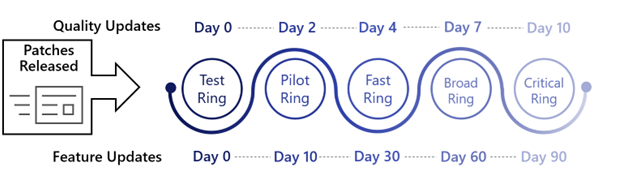
Similar to patching applications, organizations should also regularly Patch Operating Systems. Vulnerabilities in operating systems can be exploited by cybercriminals, making it crucial to keep them updated.
7. Multi-Factor Authentication
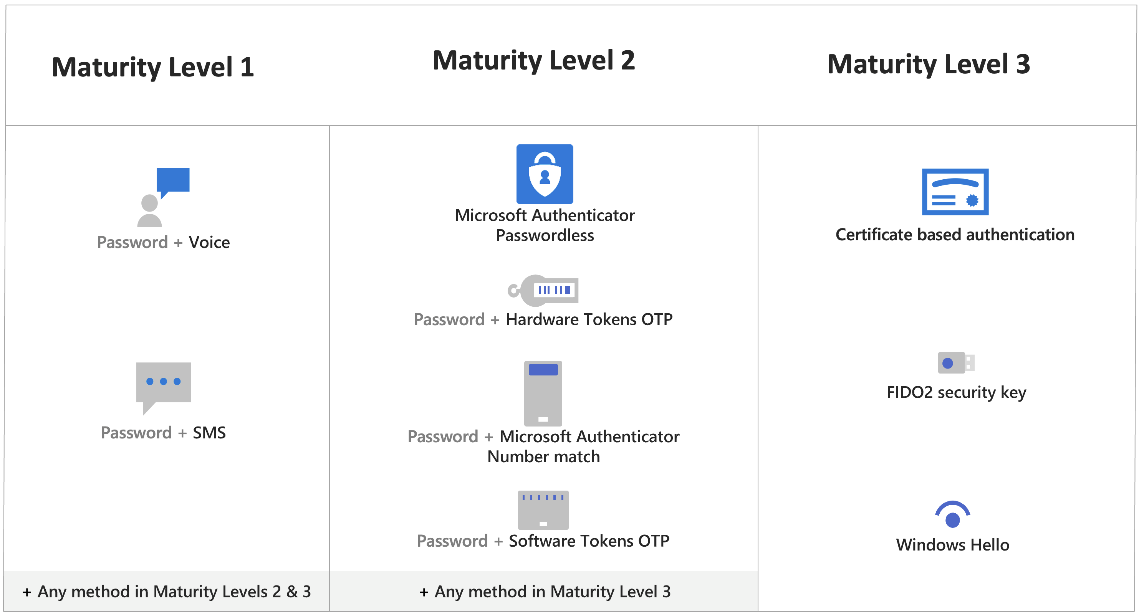
Multi-Factor Authentication (MFA) adds an extra layer of security to user logins. It requires users to provide two or more authentication factors before granting access, significantly enhancing security.
8. Daily Backups
Daily Backups are a critical part of any cyber security strategy. Regularly backing up data ensures that in the event of a cyberattack, data can be restored without significant loss.
Implementing the Essential 8 Framework
To effectively implement the Essential 8 Security Framework, organizations should take the following steps:
- Assessment: Begin by assessing your organization’s current cyber security posture. Identify strengths and weaknesses to tailor your approach.
- Prioritization: Prioritize the strategies within the framework based on your organization’s specific needs and vulnerabilities.
- Education and Training: Ensure that your team is well-informed about the Essential 8 strategies and the role they play in maintaining security.
- Regular Updates: Regularly review and update your security measures to adapt to the evolving cyber threat landscape.
Strengthening Your Cyber Security
Cyber security is paramount in the digital age. The Essential 8 Security Framework offers a structured approach to safeguarding organizations from a wide range of cyber threats. By diligently implementing these strategies, organizations can significantly enhance their cyber security posture and protect sensitive data.
Connect with Us on LinkedIn
In a world where cyber threats loom large, procrastination can be costly. Take a proactive stance to safeguard your digital assets by embracing the Essential 8 Security Framework before it’s too late. Connect with us on LinkedIn to tap into a network of professionals who, like us, are fervently dedicated to driving meaningful business transformations through technology.






