Limiting access to all apps in Microsoft 365 is crucial; unrestricted access isn’t advisable. Controlled restrictions are necessary for each app and service. Microsoft Azure’s Conditional Access aids in this regard.
This piece delves into the significance of conditional access and its implementation in Microsoft 365 to manage app access.
Why restricts access?
Considering access to all apps for everyone in the organization, regardless of relevance or usage, warrants careful consideration. Implementing access restrictions can prove beneficial in the following scenarios:
- Applying limitations to licensed app usage.
- Implementing a phased rollout of services, initially accessible to pilot users.
- Improving license assignment through group allocation instead of random individual allocation.
- Enhancing app and organizational security measures.
What is Conditional Access?
Conditional access functions similarly to an if-then statement. It follows the logic that if a user requires access to a resource, they must fulfill a specific condition or complete a designated action in order to obtain that access.
Involve Conditional Access to Microsoft 365 Apps
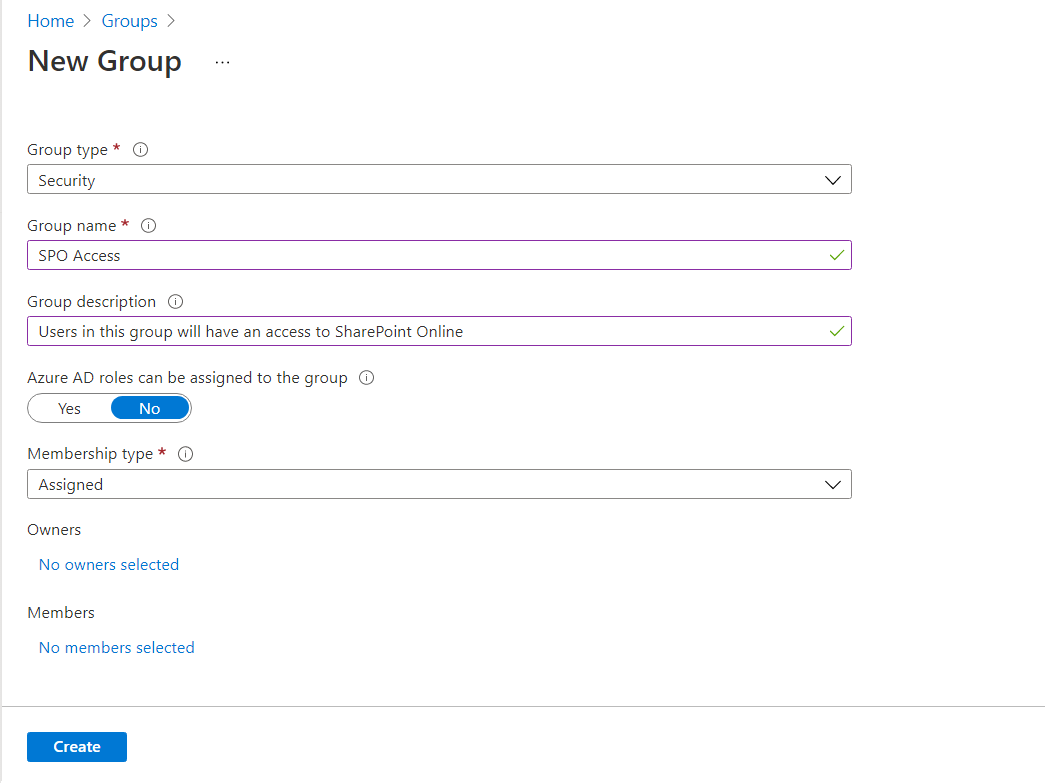
Azure AD Security Group
Include provisions for granting access to the app through the Azure AD security group during the planning phase.
Conditional Access Policy
To create a new conditional access policy, follow these steps:
- Log in to the Azure portal with the appropriate credentials.
- Navigate to the Azure Active Directory service.
- Select “Conditional Access” from the left-hand menu.
- Click on the “New Policy” button to create a new policy.
- Provide a descriptive name SPO Access Policy.
- Under Assignments > Users or workload identities, exclude our AAD security group.

- Specify the cloud apps or actions that the policy will target. You can choose specific apps, all apps, or a combination.

- In the Conditions section, select the option to include apps as depicted.

- In the Access Controls section, select Block Access under the Grant option.
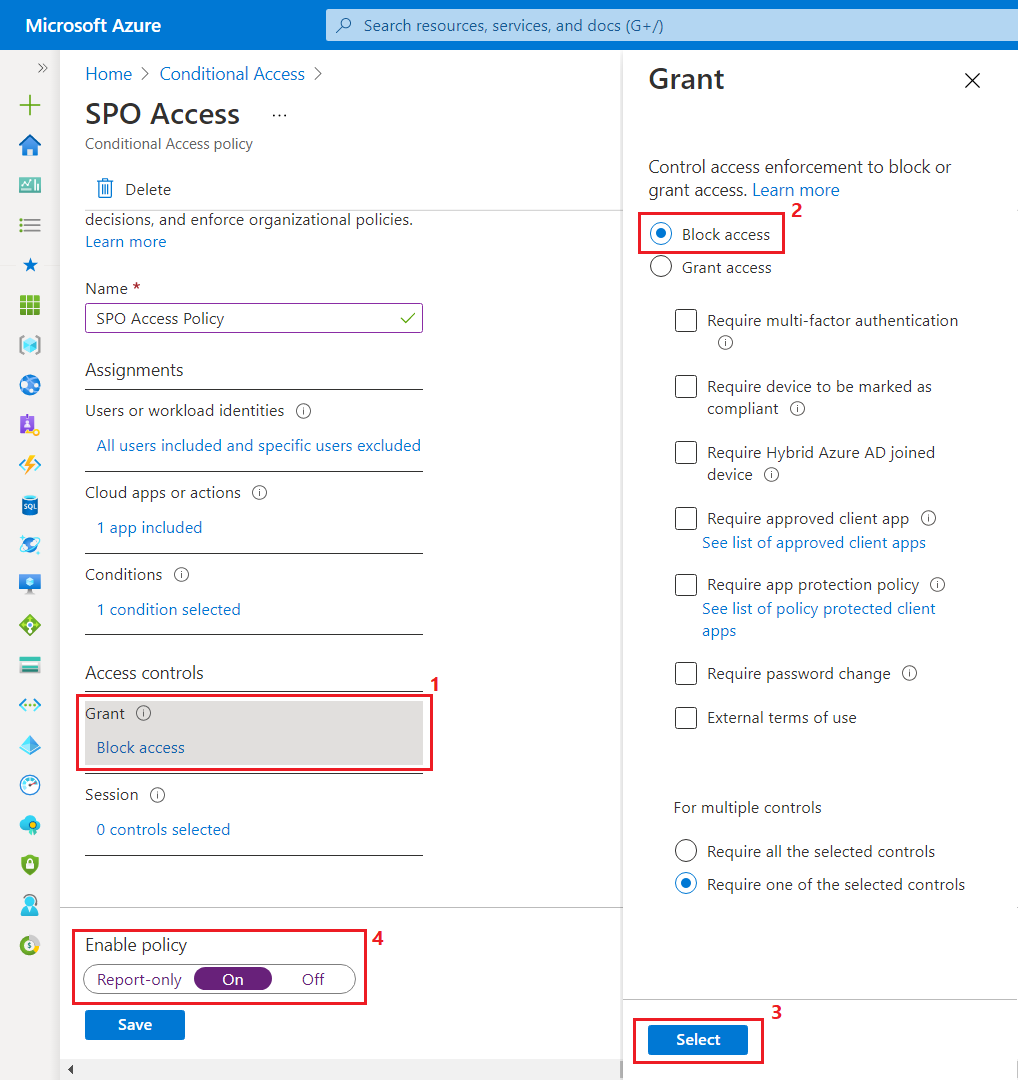
- Enable the policy and save the changes.
Note: The specific steps and options may vary slightly depending on the Azure portal’s version and your Azure environment’s configuration. It is recommended to refer to the official Azure documentation for detailed instructions and the most up-to-date information on creating conditional access policies.
Test the Policy
Members of the AAD security group named SPO Access are granted browsing privileges for the SharePoint sites, while non-members will encounter the specified error message.

Debug/Fix the access issue
To identify the root cause when a user encounters an access issue due to a conditional access policy, follow these steps:
- Open the Azure AD portal again.
- Navigate to the Users section.
- Search and select the user who is experiencing the access problem.
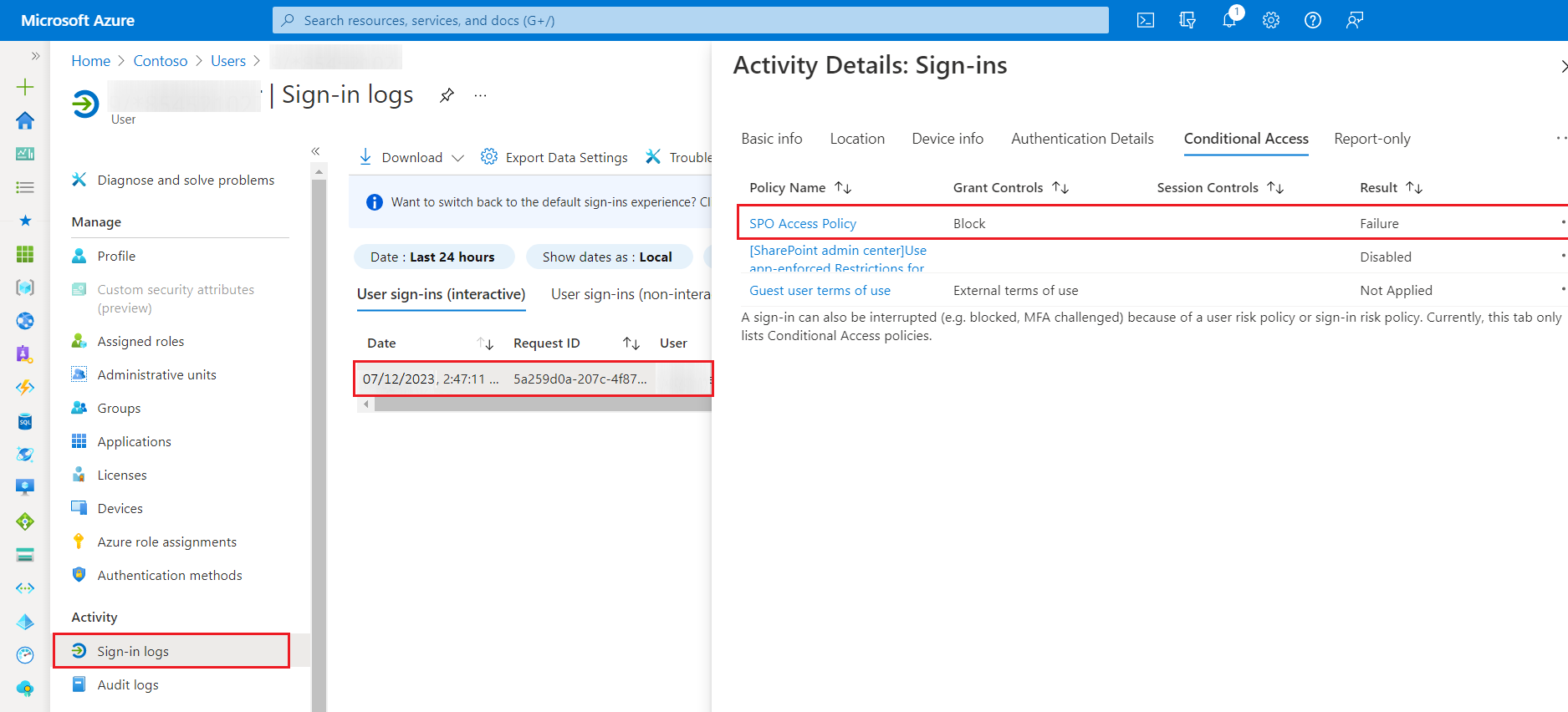
- Under the Activity tab, click on Sign-in logs.
- Look for the specific sign-in entry that resulted in a failure for the user in question.
Summary
In order to ensure controlled access, it is essential to restrict access to each app and service within Microsoft 365. Microsoft Azure’s Conditional Access is highly beneficial in such scenarios, providing the means to enforce specific conditions and policies to regulate access.
By leveraging Conditional Access, we can ensure that the right level of access is granted to the appropriate individuals, enhancing security and mitigating risks. With expertise in implementing Conditional Access, TECHOM Systems can assist you in optimizing access control throughout Microsoft 365, fostering a safer and more efficient work environment.