Employees and IT alike may have more freedom thanks to cloud computing. In addition, it presents additional obstacles to keeping your company safe. Cloud applications and services will be ineffective unless an IT team finds the appropriate mix of enabling access while retaining control over data that is crucial to the business.
Microsoft Cloud App Security, a Cloud Access Security Broker (CASB), could also be deployed during a sort of ways, including log collecting, API connections, and reverse proxy. It offers comprehensive visibility, data travel control and advanced analysis to detect and fight cyber hazards across all Microsoft and cloud services of third parties.
Microsoft Cloud App Security is built with security experts in mind and interacts with Microsoft products. The product’s deployment, centralised administration, and inventive automation features are easy to use.
Why does a CASB matters to you?
It would help if you had a CASB to comprehend better your entire cloud posture, which includes discovering and controlling shadow IT and cloud services. Thus SaaS applications are essential to use cases. A company must also be in charge of protecting its cloud, including setting up IAM, virtual machines, and the computing resources, data, and storage involved. If you are an enterprise utilising, or planning to employ, cloud applications to the network, you will likely require a CASB to handle the issues that these new applications bring. You might, for instance, point out that cloud applications provide a range of opportunities for bad actors to sneak into your corporate network and steal your company’s critical data.
As an entity, you must safeguard your customers and private information from hostile adversaries. To assist you to do this, CASBs provide a broad range of capabilities that may protect your environment within the following categories:
- Discoverability: identify all cloud services, assigning them a risk rating; discover all user and third-party applications allowed to log in.
- Information security: Know and control sensitive data (DLP); provide adaptive access control (AAC) to react to categorisation labels on material; provide user and entity behaviour analysis (UEBA) and malware mitigation
- You must: report supply, and keep up-to-date dashboards to prove control of the cloud; help with attempts to comply with data residency and regulatory compliance rules.
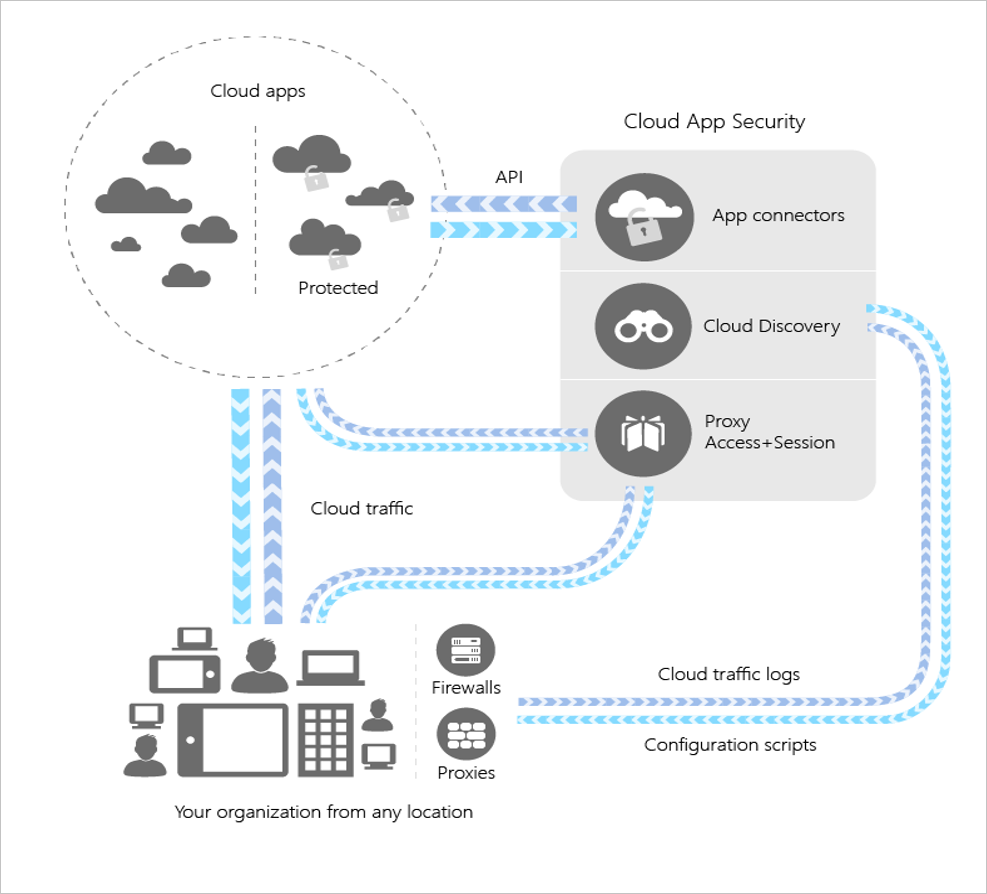
Microsoft Cloud App Security Architecture
Find and manage the usage of shadow IT: Discover what applications, IaaS, and PaaS products your company uses. Conduct research on use trends, evaluate the risk levels of over 16,000 SaaS applications and assess their business preparedness against more than 80 hazards. Then, to secure the system and guarantee compliance, begin monitoring them.
Safeguard critical information regardless of the cloud service you use: Protect the exposure of sensitive data by understanding, classifying, and protecting it when at rest. Use advanced techniques like automated rules and real-time controls to implement control measures across all your cloud applications.
Protect against cyber threats and anomalies: Employ automation to detect, identify, and fix problems quickly to help protect your business from dangers like ransomware, rogue programmes, and compromised users.
Check your cloud applications’ compliance: Evaluate your cloud applications for regulatory compliance and industry standards, including regulations. Protect data from being shared with unsecure applications, and restrict access to data subject to regulatory oversight.
Microsoft Cloud App Security delivers more visibility to your cloud applications by integrating with it:
- Map and identify your cloud environment and the cloud applications your business is utilising by using Cloud Discovery.
- You are making and breaking the rules for applications in your cloud.
- The ability to connect and regulate applications using pre-deployed connectors that use provider APIs.
- Real-time control and visibility over access and activity in your cloud applications with Conditional Access App Control.
- By establishing and fine-tuning policies, we provide you with ongoing control.